Using open data to combat transnational criminal networks
14 February 2016
By Varun Vira and Jessica Hansen, C4ADSOver the past decade the global security environment has evolved, allowing rogue nation-states, sanctioned terrorist organizations, and violent criminal syndicates to operate on a transnational scale, converging in pursuit of common objectives. Today, these illicit actors are deeply embedded within international systems of finance, commerce and transportation, threatening to critically undermine the foundations of global peace and prosperity. This article highlights C4ADS’ approach to analysing unclassified data in order to demonstrate how illicit networks operate, thereby empowering law enforcement authorities, logistics companies, and financial institutions to take action against transnational organized crime.
The new generation of illicit actors is inter-connected, globalized, and technologically savvy. Nuclear proliferators maintain complex webs of proxies and shell companies to evade international sanctions, and pariah states use similar networks to arm and equip their surrogates around the world. Meanwhile, international terrorist organizations and other perpetrators of mass atrocities operate multi-billion dollar commercial empires with global reach, funneling proceeds through Western jurisdictions.
Globalization, and the unprecedented access to information and technology that followed, has sponsored the success of these illicit networks. However, policymakers and law enforcement officials can harness the same proliferation of open data, which enables these criminal actors, to deny their rise and halt their operations. Digitized global public records, multilingual news sources, and communications access to the most remote corners of the world, represent enormous sources of information that can be mined to expose and disrupt illicit networks.
This proliferation of data creates a new opportunity for open source investigations to provide real world results, proving that actionable intelligence is no longer strictly limited to governmental organizations. From this environment, a new generation of agile and technology-driven institutions, with the flexibility and capacity for innovation, are emerging to meet the demands of the evolving security climate.
C4ADS, a non-profit organization, specializes in open source analysis on the enablers and facilitators of illicit networks and conflict systems. By leveraging cutting edge technology to manage, integrate, and analyze data from diverse languages, regions, and sources, we provide evidence-driven, non-partisan analysis on a range of first tier threats, including terror financing, trade-based money laundering, arms trafficking, environmental crime, and kleptocratic asset tracing. Our analysis has led us to develop several key insights into the fundamentals of open source investigations.
First, investigating illicit enterprises requires an understanding of the international businesses, markets and financial institutions that illegal actors seek to exploit. Accessing business directories, tax registries, property listings, court documents, intellectual property records, and official trade gazettes from diverse jurisdictions yield huge volumes of data. When combined with the correct analytical approach, this data can reveal vast illicit financial enterprises.
Second, analysts seeking to counteract illicit networks must match their global reach. This requires developing an integrated unit of analysts with varied lingual and regional specialties that can share information between seemingly separate investigations. Through coupling open source data with local knowledge, these investigations frequently uncover high levels of convergence across illicit vertical markets.
Third, cutting-edge technology is required to effectively manage high volumes and varieties of data. Network analytical tools, such as those developed by Palantir Technologies, help structure data and enable analysts to quickly identify patterns, trends, and visualize networks. When combined with a multitude of other analytical platforms, geospatial modeling programs, and statistical tools, big data can be structured and explained in an easily digestible manner.
The advantages of open data have been clearly demonstrated in several high-profile investigations that have resulted in action against narcotics kingpins, environmental product traffickers, and facilitators of money laundering schemes. These illicit actors have proven they have the ability to quickly shift their methodologies and procedures to avoid detection. This flexibility necessitates that private institutions combating these criminal enterprises remain equally agile. Institutions that succeed in maintaining independence from bureaucratic constraints are best positioned to match and rapidly adapt to dynamic changes in illicit networks.
Environmental criminal networks have become an issue of growing concern for the international community; according to the latest available figures from the United Nations Environmental Program, illicit environmental trade may generate 100 billion USD in revenues annually. The trade in illicit ivory products contributes substantially to this number.
C4ADS maintains one of the world’s most extensive ivory seizure databases, with over 900 seizure instances between 2009 and 2015, as well as 20,000 individuals and entities identified in relation to ivory trafficking operations. Housed in Palantir, an analytic platform used worldwide by the intelligence, defence, and law enforcement communities, the ivory seizure database is structured so emerging trends and networks can be easily identified and tracked over time. Each entity is extensively tagged with qualitative data including bills of lading, Customs press releases, judicial documentation, and company registrations and tax records for entities associated with a specific trafficking instance.
By structuring big data in an accessible way, our ivory seizure database helps provide actionable analysis to law enforcement bodies mandated to address the illicit trade in environmental products. In addition to tracking trends, the database allows analysts to map transnational criminal networks, identifying new developments that can assist Customs agencies in refining screening and targeting processes.
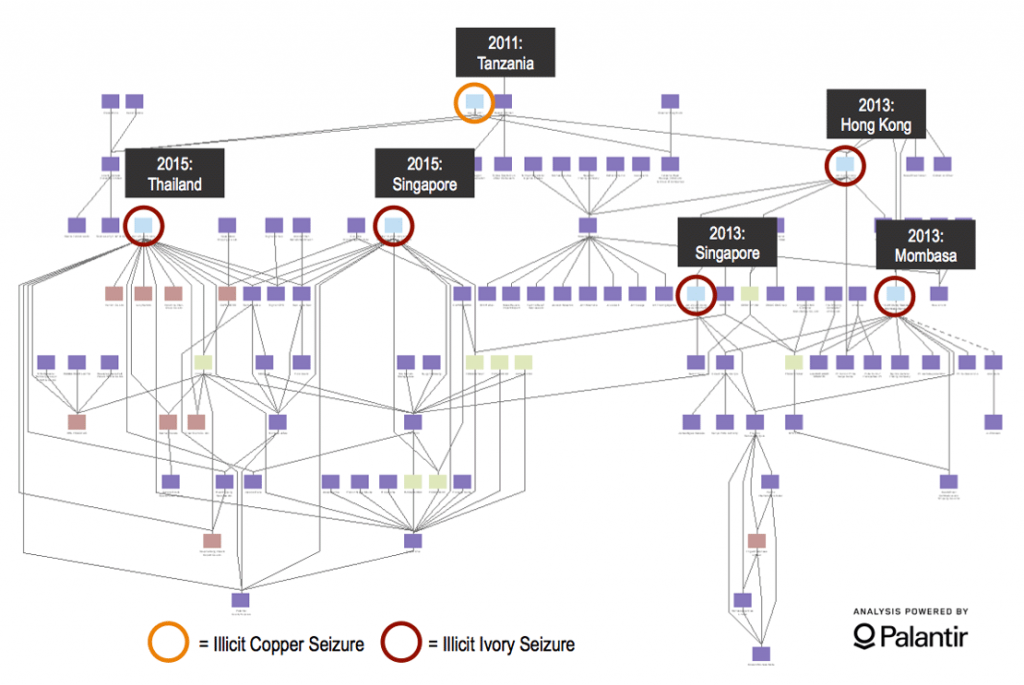
In 2015, two large ivory seizures in South East Asia demonstrated how properly structured data may help refine Customs screening protocols. The following investigation identified a transnational ivory trafficking network connected to five ivory seizures, totaling 13 tons of ivory, in several countries. The 2015 ivory consignments, although at first glance unrelated, were both declared as tea leaves, exported by the same shell company, and shipped from the Port of Mombasa in Kenya. The shell company, likely established as a front for ivory exports, was linked to several freight forwarders, trucking agents, export companies, and individuals suspected to have facilitated at least three other un-seized ivory shipments.
The investigation identified several weaknesses that may aid Customs officials in enhancing screening and enforcement protocols. First, at the time of export, shipments declared as tea leaves were exempt from additional screening at the Port of Mombasa in order to expedite trade for one of Kenya’s major industries. Traffickers were not only aware of such loopholes, but actively exploited them. Although this loophole was eliminated in response to the seizures, similar analysis could help to identify other weaknesses in port policies.
Second, the vehicle that delivered the containers of ivory to the Port of Mombasa was known to have previously delivered ivory shipments to Mombasa in 2013. This vehicle was known to Kenyan government authorities, but was not included on a watch list at the port, highlighting the potential need for more frequent communication and updates between government and Customs watch lists.
Finally, the consignee for the shipment was changed several times following export. The containers were originally assigned to a consignee in Dubai, and therefore did not receive the additional screening usually associated with East Asian destinations. Following their export, the destinations of the containers were changed several times, and eventually sent to a company in Vietnam. Changes made while containers are en route, such as these consignee changes, frequently seek to obfuscate the destination of illicit shipments.
Identifying such red flag indicators could have alerted Customs authorities in Dubai to the movement of an illicit shipment. Analysis on these seizure instances and the mechanisms that the traffickers used to successfully export the consignments are part of larger trends in ivory product trafficking which may help Customs authorities enhance screening measures for key high-risk ports and entities in the future.
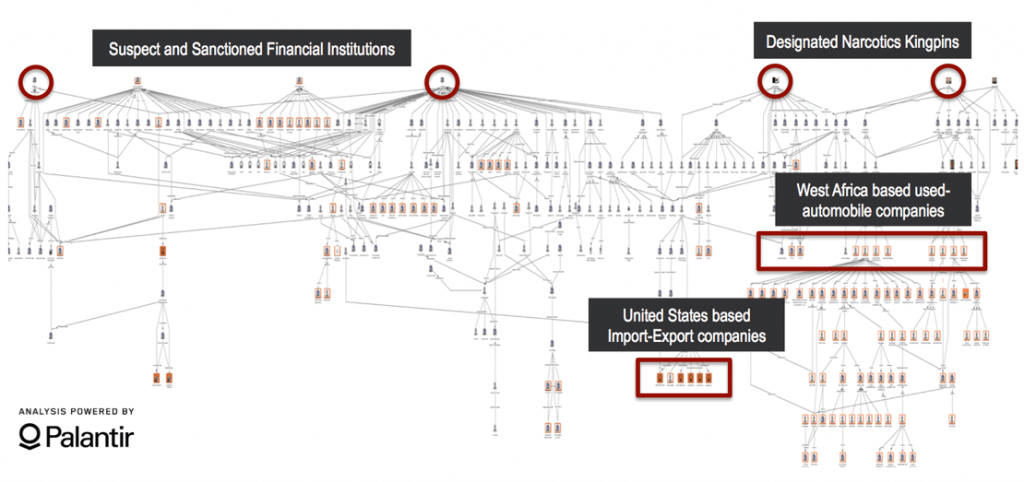
Other investigations highlight the extent to which transnational organized criminal syndicates nest their activities within licit systems of trade and commerce. In 2015, we investigated a West Africa based financial network with alleged ties to terror financing. The network operated trade based money-laundering schemes through sanctioned financial institutions, using used automobile businesses and import-export companies owned by several known narcotics kingpins in West Africa.
Using publically available, official documentation, C4ADS expanded the network to identify beneficial ownership structures, revealing that multiple companies within this network had overlapping executives, shareholders, and addresses with previously sanctioned entities. In addition to points of high-risk convergence for terror financing activities, several entities shared addresses with companies that maintained trade relationships with businesses in the United States (US). The resulting network exposed a global web of companies managing several illicit operations, including narcotics trafficking, money laundering, and wire fraud.
The connections C4ADS established between known terror financing entities and used automobile money laundering schemes resulted in enforcement action. The links between these sanctioned entities and the companies engaging in trade relationships with the US demonstrated that even the world’s most closely monitored financial institutions and Customs agencies are still vulnerable to criminal exploitation, and can therefore highly benefit from open source analysis.
More information
www.c4ads.org
info@c4ads.org